OT Security
25.Apr.2024
Security Development in the Industrial Control Field! Myths and Key Concepts
With the rapid development of the Industrial Internet of Things (IIoT), modernized factories and production lines are increasingly depending on industrial control systems with Internet connections to maintain operations. However, the cybersecurity threats on OT systems are often underestimated or ignored by businesses.
Dong-Ying Li, an Onward Security consultant, points out that OT systems are fundamentally different from regular IT systems in terms of cybersecurity priorities. "In the IT field, data confidentiality is usually the priority, followed by integrity, and lastly, availability. But for OT systems, availability is the most critical, since the entire production line can be paralyzed if the system fails to operate normally."
Li emphasizes that many businesses mistakenly believe that isolating OT systems from external networks or deploying firewalls can ensure security. This is a dangerous misconception. "Even if the system is not connected to the network, it can still be discovered and invaded by hackers. Moreover, firewalls can rarely be configured perfectly, and internal employee misconduct also poses significant security threats to industrial control systems."
Furthermore, businesses often assume that hackers won't target industrial control systems because of their perceived simplicity. However, this is not the case. "There is already a vast amount of information about industrial control systems on the Internet, and some botnets specifically target such systems. As long as hackers can paralyze a production line and achieve their destructive goals, they don’t need to fully understand the system's operating principles."
Dong-Ying Li, an Onward Security consultant, points out that OT systems are fundamentally different from regular IT systems in terms of cybersecurity priorities. "In the IT field, data confidentiality is usually the priority, followed by integrity, and lastly, availability. But for OT systems, availability is the most critical, since the entire production line can be paralyzed if the system fails to operate normally."
Li emphasizes that many businesses mistakenly believe that isolating OT systems from external networks or deploying firewalls can ensure security. This is a dangerous misconception. "Even if the system is not connected to the network, it can still be discovered and invaded by hackers. Moreover, firewalls can rarely be configured perfectly, and internal employee misconduct also poses significant security threats to industrial control systems."
Furthermore, businesses often assume that hackers won't target industrial control systems because of their perceived simplicity. However, this is not the case. "There is already a vast amount of information about industrial control systems on the Internet, and some botnets specifically target such systems. As long as hackers can paralyze a production line and achieve their destructive goals, they don’t need to fully understand the system's operating principles."
Security Development Concepts
In response to these security concerns, the industry is gradually adopting the concept of the Security Development Lifecycle (SDLC), aiming to incorporate cybersecurity at every stage of product development. The SDLC consists of seven steps:
1. Education and Training: Ensuring that all team members involved in development have a basic understanding of cybersecurity, and are aware of common threat patterns, protective measures, and most importantly, the method of conducting secure programming.
2. Requirements Analysis: Beyond general functional requirements, carefully analyze the product's cybersecurity needs and design corresponding security mechanisms. In this step, businesses need to pay special attention to the following:
- Analyzing the necessary security features of the product, not just focusing on general functional requirements.
- Identifying potential security risks and threats in the product's usage scenarios, creating a comprehensive security landscape.
- Using threat modeling methods to identify hidden potential threats and provide a basis for subsequent design.
3. Design: Adopting the "defense in depth" design philosophy, implementing security protections for all module and interface levels. In the meantime, also refer to industry best practices to enhance design security.
4. Security Implementation: Strictly following secure programming standards while also constantly reviewing and fixing security vulnerabilities through source code scanning and software bill of materials (SBOM) management. During this stage, businesses should stay cautious about the following:
- Ensure the development team adheres to secure programming standards and best practices.
- Use automated source code scanning tools to identify and fix known vulnerabilities.
- Establish a Software Bill of Materials (SBOM) to identify security risks hidden in third-party components.
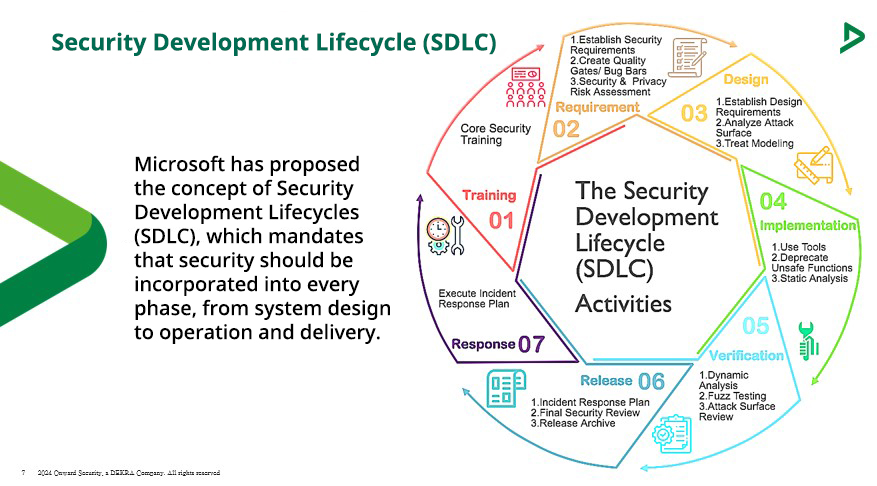
5. Security Verification: Conducting specialized security testing, including security feature testing, threat mitigation testing, vulnerability detection, and penetration testing, in addition to general functional testing. Ensuring the independence of testers is especially crucial for objective system security evaluation. This approach ensures the objective evaluation of system security and the effective assessment results. During this phase, businesses should focus on the following:
- Thoroughly test the product's security features to ensure effective defense against known threats.
- Perform targeted mitigation measures testing based on identified potential threats in the threat modeling phase.
- Use both automated and manual methods to thoroughly check for known security vulnerabilities.
- Invite professional independent teams to conduct penetration testing and simulate real attack scenarios.
6. Secure Release: Carefully assess residual risks before product delivery and provide users with relevant security guidelines.
7. Security Incident Response: Establish mechanisms for reporting, analyzing, and rapidly resolving security incidents, to adequately address potential future security events; Another focus shall be the development and release of patches after vulnerabilities are discovered.
Li emphasizes that merely relying on technical means is far from sufficient to truly enhance OT system security. "The most critical factor is changing the security awareness and management approach of enterprises.” For example, many businesses neglect the software upgrades of industrial control systems, concerning that production line operations might be interrupted. "But if an attack paralyzes the whole business, the losses incurred are often far greater than those from a temporary shutdown for an upgrade.”
Therefore, businesses must place significant emphasis on the management of cybersecurity protection for OT systems, systematically promoting various security measures following the SDLC as a blueprint. Only in this way will they effectively reduce the cybersecurity risks threatening industrial control systems, ensuring the stability and reliability of production.
1. Education and Training: Ensuring that all team members involved in development have a basic understanding of cybersecurity, and are aware of common threat patterns, protective measures, and most importantly, the method of conducting secure programming.
2. Requirements Analysis: Beyond general functional requirements, carefully analyze the product's cybersecurity needs and design corresponding security mechanisms. In this step, businesses need to pay special attention to the following:
- Analyzing the necessary security features of the product, not just focusing on general functional requirements.
- Identifying potential security risks and threats in the product's usage scenarios, creating a comprehensive security landscape.
- Using threat modeling methods to identify hidden potential threats and provide a basis for subsequent design.
3. Design: Adopting the "defense in depth" design philosophy, implementing security protections for all module and interface levels. In the meantime, also refer to industry best practices to enhance design security.
4. Security Implementation: Strictly following secure programming standards while also constantly reviewing and fixing security vulnerabilities through source code scanning and software bill of materials (SBOM) management. During this stage, businesses should stay cautious about the following:
- Ensure the development team adheres to secure programming standards and best practices.
- Use automated source code scanning tools to identify and fix known vulnerabilities.
- Establish a Software Bill of Materials (SBOM) to identify security risks hidden in third-party components.

- Thoroughly test the product's security features to ensure effective defense against known threats.
- Perform targeted mitigation measures testing based on identified potential threats in the threat modeling phase.
- Use both automated and manual methods to thoroughly check for known security vulnerabilities.
- Invite professional independent teams to conduct penetration testing and simulate real attack scenarios.
6. Secure Release: Carefully assess residual risks before product delivery and provide users with relevant security guidelines.
7. Security Incident Response: Establish mechanisms for reporting, analyzing, and rapidly resolving security incidents, to adequately address potential future security events; Another focus shall be the development and release of patches after vulnerabilities are discovered.
Li emphasizes that merely relying on technical means is far from sufficient to truly enhance OT system security. "The most critical factor is changing the security awareness and management approach of enterprises.” For example, many businesses neglect the software upgrades of industrial control systems, concerning that production line operations might be interrupted. "But if an attack paralyzes the whole business, the losses incurred are often far greater than those from a temporary shutdown for an upgrade.”
Therefore, businesses must place significant emphasis on the management of cybersecurity protection for OT systems, systematically promoting various security measures following the SDLC as a blueprint. Only in this way will they effectively reduce the cybersecurity risks threatening industrial control systems, ensuring the stability and reliability of production.







